Here are the archived challenges from our 2022 Email Forensics CTF.
| Quick Stats | |
|---|---|
| Started | February 9, 2022 |
| Ended | April 21, 2022 |
| Top 3 | Sam Greenwald, Zach Stanford, Phill Moore |
Week 1: To Read, or Not to Read
You have exported the contents of a Gmail mailbox via Takeout. Looking at the exported data1, you suspect that one of the top-level messages may have been read by the perpetrator. Enter its Message-ID (i.e., the value of its Message-ID: header field as defined in RFC 5322).
takeout-20220209T193226Z-001.zip (~24.4 MB)
1SHA-256: F77C28E0DCC8481279CF99F79DCAD3E5EAE755884D335BD61B7ED13C34E8FD28
Week 1: To Read, or Not to Read—Part 2
Congrats on locating that message!
You are now examining the message you identified during the first part of this challenge. One of the header fields gives you pause about the authenticity of the message. Which header field is it?
Enter the name of the header field, including the colon.
Week 2: Gulliver
You are asked to examine an Outlook message1. This message was found within an Outlook data store and differed from its neighbors, as in the screenshot below:
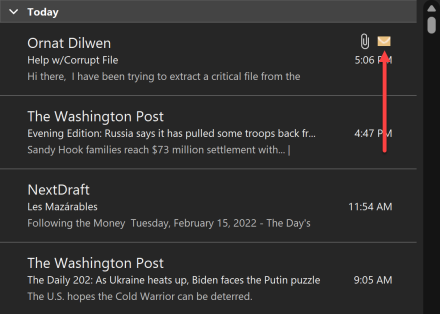
Specifically, even when the message was read, Outlook displayed a yellow envelope icon next to the message within a folder.
After analyzing the message, you found that a MAPI property is responsible for the above behavior. Which MAPI property is it?
Enter the 2-byte hexadecimal identifier of the corresponding canonical MAPI property.
Hint: The range of property identifiers runs from 0x0001 through 0xFFFF.
1 Help w_Corrupt File.zip (~ 368 KB)
SHA-256: 138168D25656AE7816C0AB41438E38BBF2F1A6B17AC4B5D10A4C27CEC1F8B48A
Week 2: Gulliver—Part 2
You now direct your attention to the contents of the message you examined in Part 1 of this challenge.
Extract the critical business document contained within GOAT.zip in its entirety, and enter its MD5 hash.
Week 3: Can’t Touch This
You have forensically preserved emails from an Outlook.com mailbox in MIME format. One of the emails1 contains crucial evidence. Unfortunately, DKIM verification fails for this email of interest.
Based on prior experience, you believe that the failure of DKIM verification is caused by changes that were made to the message body automatically by Microsoft’s email server. Roll back Microsoft’s changes to the message body by making as few changes as possible, and bring the message to a state where both DKIM signatures are verified. Once you get there, enter the total size of the resultant EML file in bytes.
1Write This Down.zip (~5.3 KB)
SHA-256: 406369232D3C59CF035211272661958A4B154D663A1BD0AFE4DCA8732182A940
Week 3: Can’t Touch This—Part 2
Great work! You have managed to roll back the changes and arrived at a message where DKIM signatures are verified.
Currently, the DKIM-Signature: header field specifies the digital signature algorithm as rsa-sha256, resulting in a body hash value of g0TrqSdjpUvQgXxwp2JBFfTNzRigCGQsTZyrab3/qyo=. What would the body hash have been, if the algorithm were rsa-sha1 instead?
Note 1: Perform your calculations using the new message you created during Part 1 (i.e., the message where DKIM signatures are successfully verified).
Note 2: Enter the body hash in the form it would have appeared in the bh= tag.
Week 4: Time Machine
You have located a key email message1 within the forensic image of a suspect’s computer. Based on intelligence you previously received, you have reason to believe that the email message was altered after the original email communication took place, and exactly one complete sentence was added to the body of the message.
Enter that extra sentence, including the period at the end of the sentence.
SHA-256: 1B5273A90B2CB3416D849BECDED33308390FA2F4CEB0F9E96B39CCAB8ADE8E27
Week 5: Lucre
You are investigating a financial crime where the suspects are believed to be hiding cryptocurrency private keys in email messages.
An important email message1 is found within the forensic image of a suspect’s laptop. What is the hidden key?
SHA-256: 47A453B56B47C50C06D521340DDF779BB14E067F03554F836A527C596410FE99
Week 5: Lucre—Part 2
Congrats on finding that hidden private key! What is the corresponding public key?
 — Week 1 - 5 Answers & Solutions —
— Week 1 - 5 Answers & Solutions —
Email Forensics Workshop—2022 CTF Solutions - YouTube
Week 6: Leprechaun
As you continue your investigation of the forensic image in the last challenge, you come across an additional email1 where the suspects appear to be transmitting a sensitive document.
Find the hidden document, and enter the fourth item on the referenced checklist.
1Plans for Today.zip (~27.9 KB)
SHA-256: 11D839BE43778EDB01F20C301E26537AB574203793DF79A2113F1FE5F614EA08
Week 7: Burning Ship
You are asked to examine a crucial communication1 between two suspects. Upon reviewing the message, you suspect that one of its header fields may have been removed. Enter the name of the header field, including the colon.
SHA-256: 7D6B36948E46D1D415E98E2AA4366AB5493E57D2718B5998D841219B465B6305
Week 7: Burning Ship—Part 2
As you turn your attention to the contents of the message you examined in Part 1 of this challenge, you notice that a word was redacted (i.e., replaced with the string REDACTED).
Recover the redacted word and enter it as your answer.
Week 8: Trebuchet
During your investigation of a hosted email account, you encounter an email message of interest with the following identifier:
AAMkADBmNjNjZDgwLWNmNDgtNGQxYy1hMzVjLTM2NjgxNGI0OGE5ZQBGAAAAAADPupqIU5ELTZOK+Q1jA7uiBwBkSTUbboy6QKrdyXLaUEMtAAAAAAENAABkSTUbboy6QKrdyXLaUEMtAAgBGeyPAAA=
You are being asked to find the MessageGlobalCounter value for this message — a 6-byte unsigned integer that identifies the message.
Enter the MessageGlobalCounter in decimal form.
Week 8: Trebuchet—Part 2
You have now located 11 additional message identifiers1.
Which message identifier belongs to a message that is in the same folder as the message you examined in Part 1 of this challenge?
SHA-256: 325A75DE0565A473E180F43C1F52E204F8818C0C163826CCF455810A72C4685B
Week 9: Barrel Roll
You have forensically preserved a subset of a suspect’s mailbox. Upon reviewing the acquisition log1, you suspect that one of the mail folders included in your acquisition was recently created, and messages were added to it after the fact.
Based on the information available to you, when was this recently-created folder likely created? Enter your answer in UTC, in yyyy-MM-dd HH:mm format (24 hour time). Example: 1987-01-28 13:41
SHA-256: CDCC3A7CAD8081DBAB0874D1AA7DBA747B4E818139F588E00382A58679D24017
Week 9: Barrel Roll—Part 2
You continue to review the same acquisition log as in Part 1 of this challenge. Based on the information available to you, when was this mailbox likely created?
Enter your answer in UTC, in yyyy-MM-dd format. Example: 1987-01-28
Week 9: Barrel Roll—Part 3
Upon reviewing the acquried messages and the same acquisition log discussed in Part 1 of this challenge, you suspect that one of the messages in the Sent folder had been modified and synced back to the email server.
Based on the information available to you, when was the altered email likely uploaded to the server? Enter your answer in UTC, in yyyy-MM-dd format. Example: 1987-01-28
Week 10: Hopper
While examining the forensic image of a suspect’s device, you come across the following information associated with the email account ornatdilwen@outlook.com.
Important Note: The token below was time sensitive and is no longer valid since the CTF finished.
Token
M.R3_BAY.-CfAoYqYTOQ*kRdYPVHmNK2unJwwpUubTGgpnZKL!2V47vjURV5svwQC4CpT1Ndf5SijVn7msoGp!*f8S7Yz9V6y7bPAqZ!v3WCBCoZ9ZXwHtV!cQfEgYl1spXllCxjgdIzXAt0W4cZ9nSaXlci9cL8u4TAFnBj0QaJfHAOVIwxKw0k1Ay8Hsxw1uL3Dzrm*KPAO3*oh4uytOSQSGO9!!jrqDXUXptr1WHVf6ogb*arHmiowl3PPOlsn3jAdx8STPKPMVkOEYOVAEqEiwxOgu6SFw4JzTTAaSsTQVh4!xm7sMwhD9Q7r*8JXcYc5KB1jTqSl8rjqbczw7VAtK9gCMCGN2OMeEks22GfFMyBUbBrpU0FDMcRntwK3*Ies58MfjmQ$$
Client ID: c9aee94e-dd7d-4bd2-abb8-b3672347ff50
Examine the email account and enter the value of the Message-ID header field for the message that was deleted earliest.
Week 10: Hopper—Part 2
Examining the same mailbox as in Part 1 of this challenge, enter the Graph API ID of the message that was deleted on April 14, 2022 (UTC).
Note: The Graph API ID is in Base64 form, and is not the same as the Message-ID header field.
Week 10: Hopper—Part 3
Based on the information available to you, what was likely the Graph API ID of the message you found in Part 2 of this challenge before it was deleted?
 — Week 6 - 10 Answers & Solutions —
— Week 6 - 10 Answers & Solutions —
Email Forensics Workshop — 2022 CTF Solutions — Part 2 - YouTube