Hello, folks!
We’ve just released FEC v3.52. Here is a quick walkthrough of the new functionality:
S/MIME Decryption
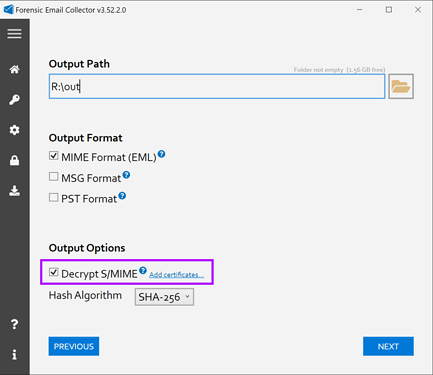
FEC now supports detecting and automatically decrypting S/MIME-encrypted items. You can turn this option on within the Output Settings page as follows:
Why Decrypt During the Acquisition?
You might already have a workflow in place that allows you to decrypt S/MIME offline. However, having this functionality available during the acquisition allows you to acquire Drive attachments / revisions of S/MIME-encrypted items. If you acquired in encrypted form and then decrypted offline, you would not have the opportunity to handle Drive attachments on the fly.
Output Both Ways
When FEC detects and decrypts an encrypted item, it outputs it twice: Once in its original, encrypted form (only if you choose the MIME output option), and once in decrypted form. The decrypted copy is also output in MSG and PST formats if those options are selected and used as the parent item when packaging Drive attachments/revisions with their parents.
Having the original, encrypted copy is very important because that is the format that can be used to verify DKIM.
Flexible Certificate Handling
You can supply FEC with certificates in PKCS #12 (.pfx or .p12) or DER format. If you do not supply any certificates and choose the Decrypt S/MIME option, FEC will automatically look for available certificates in that computer’s certificate store (i.e., Windows certificate store).
This can come in handy especially when performing acquisitions directly on suspects’ computers. Instead of hunting certificates down, you can have FEC automatically find them in the Windows certificate store as needed.
It is also possible to supply FEC with multiple certificates. This can be helpful if you are setting up multiple acquisition projects in batch mode and wish to supply all the necessary certificates ahead of time. Multiple certificates can also be utilized within the same acquisition project.
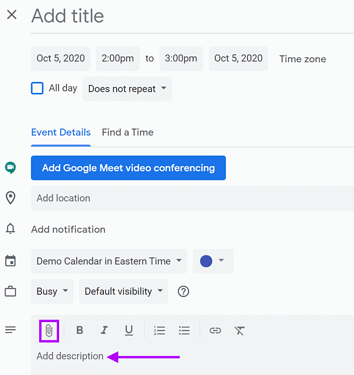
Google Calendar Drive Attachment / Revision Acquisition
We have extended FEC’s Google Drive attachment/revision acquisition capabilities to cover Google Calendar items. This supports both the Drive links in the description of a calendar item as well as items that were explicitly attached using the paperclip symbol when creating a new calendar item.
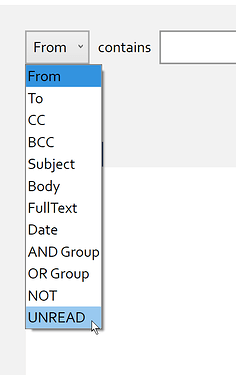
IMAP In-place Search Using the \Seen Flag
When you use the IMAP in-place search functionality, you will notice an additional search criterion named UNREAD. This will allow you to filter messages that are read or unread provided that the target IMAP server supports searching IMAP flags.
The default term searches for “unread” messages. You can look for “read” messages by adding the “UNREAD” term, selecting the added “UNREAD” term, and then applying the “NOT” operator to it as seen in the screenshot above.
This release also contains numerous performance improvements in the identification of Drive links, in-place search previews, and more. I hope you find the improvements helpful! ![]()