We have released FEI v1.8 today! Here is what’s new ![]()
MIME Structure Analysis
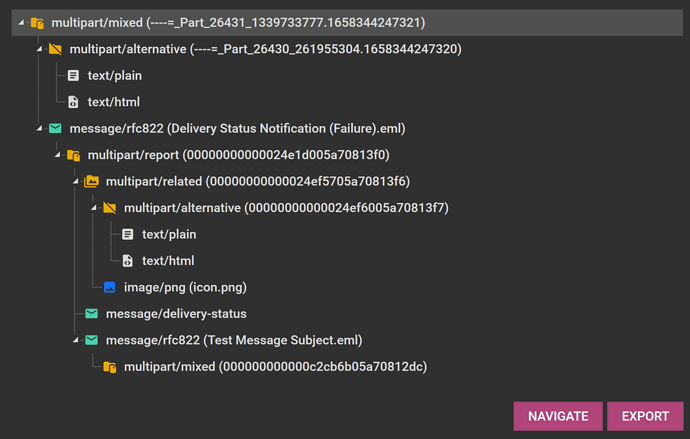
FEI now supports recursive analysis of the MIME structure of messages. That is, any child embedded messages are also traversed and their MIME structures added to the MIME structure view. Here is how the MIME structure looks for an example email:
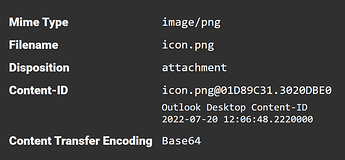
When examining the MIME structure, you will be presented with the metadata extracted from each MIME entity on the bottom half of the screen. For example:
As you examine each MIME entity, it is also possible to navigate to it in FEI’s MIME tab using the NAVIGATE button, or export it out of FEI using the EXPORT button. This makes it possible to carve out any non-attachment MIME entities within your message, or any of its children.
A huge advantage here is the ability to review a chain of MIME messages together, with their MIME structures and timestamps consolidated. This gives you an entirely different look at a group of embedded messages.
Here is a super quick walkthrough of how things fit together (~30 secs):
Child Entity Timestamps
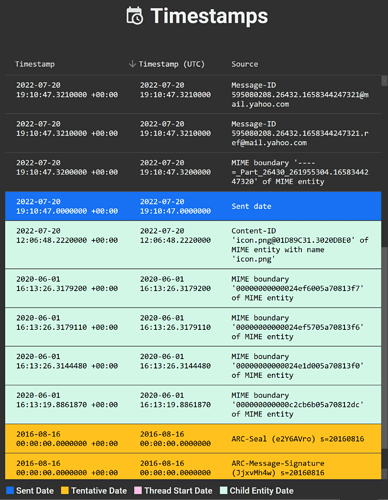
As FEI enumerates the child MIME entities within a MIME message, it often encounters hidden timing information among various data points such as MIME boundaries and Content-IDs. These are now added to the Timestamps View and color coded so that they are easily distinguishable from those of the parent message. For example:
DKIM & ARC Public Key Preservation
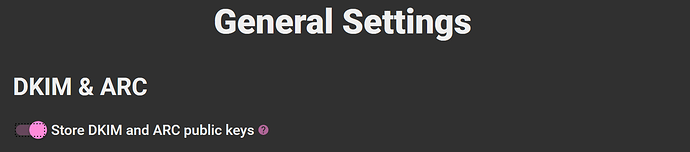
FEI retrieves DKIM and ARC public keys encountered in your target messages during batch processing and individual examination. We have added a new option to save the acquired public keys to the file system. This allows you to archive the critical cryptographic keys associated with your target messages in case they become unavailable via DNS in the future. Here is the new option that controls this behavior:
We strongly recommend utilizing this option to preserve and archive your DKIM & ARC public keys—especially if your case depends on certain messages’ passing or failing DKIM and/or ARC.
Content-ID Evidence
Content-ID values in MIME structures has been added as a new evidentiary data point for email client identification and timing information. You will start running into these in FEI’s Timestamps and MIME Structure views as well as Insights.
You can read about the additional improvements in FEI’s changelog. As usual, the installer can be found ![]() here.
here.
I hope you enjoy the new improvements ![]() I am particularly excited about MIME Structure analysis as it opens a whole host of additional investigative possibilities!
I am particularly excited about MIME Structure analysis as it opens a whole host of additional investigative possibilities!